Bypassing Android file system restrictions
As of Android 11, apps cannot access other apps’ private directories and, while it makes sense from a security standpoint, I made use of the “feature” especially to copy media files from podcast apps or messaging apps, which sometimes don’t want you to play their media files with a decent media player like VLC.
If you try to open an app’s data directory, you will reach a point where no files are listed. In this example, a podcast app data directory looks like this on a regular file browser.
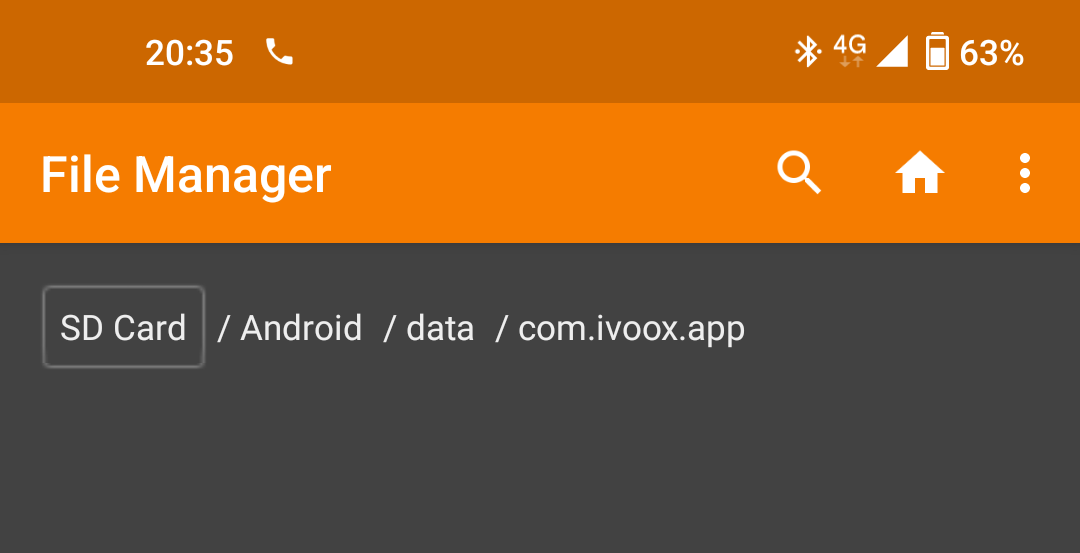
Empty. This directory should have at least one audio file that has been downloaded through the app.
It occurred to me then that, since these apps are storing their files on the SD card, that a fix could be implemented to bypass these restrictions by manipulating the filesystem structure.
Bypassing the restrictions
Most Android phones format the SD card using FAT32 if you select it for use as a media storage (not app storage) and the FAT32 filesystem design is simple and well understood, mainly consisting of groups of clusters storing data, and directory entries pointing to lists of file entries.
The plan
The plan is simple. We create an empty BYPASS directory, placed on an
unrestricted place like the SD card Downloads directory, and make it point
to the same data as the Android directory. In essence, going from this:
To this:
Getting it done
We will need a hex editor with raw disk editing capabilities. HxD
when running with admin privileges does the trick. Then open the SD card
on the editor and find the ANDROID string. That’s “Android” in all caps
followed by 4 spaces. Somewhere close to the beginning of the disk, an entry
like this will appear:
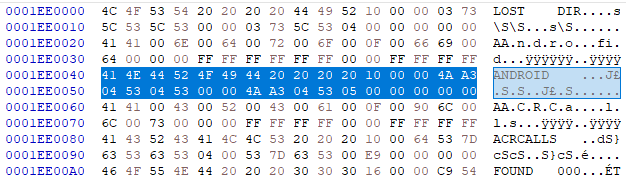
Following the FAT32 specification, the relevant parts of this data are the following:
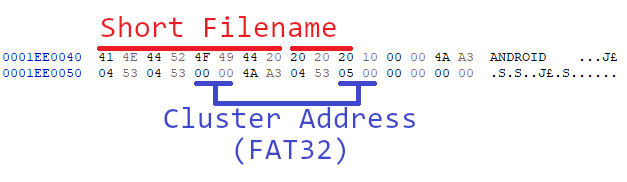
We then write down the cluster address words 00 00 and 05 00 because they
will be needed for the next step.
Open a file browser and create a BYPASS directory on any unprivileged
place like the Downloads directory, then on the hex editor search for the
BYPASS string, that is “Bypass” in all caps followed by 5 spaces. You
may use any name you like but for ease of the modifications, make sure the
directory you create is in all caps and has a length of 11 characters or less.
The hex editor will eventually find the FAT entry. Please note that it can
take long for big cards or cards with lots of data.
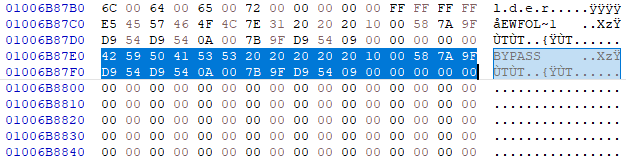
Then we replace the cluster address bytes with the ones we got from the
Android directory FAT entry.

Then after saving we can safely eject the SD card and plug it again to check if the
bypass worked. The Android directory looks something like this on the Windows
explorer:

And the formerly empty BYPASS directory now looks like this:
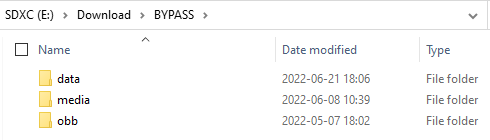
Same data, from a different place. This modification makes the FAT filesystem
inconsistent, so what may happen if you modify the data or run chkdsk on it
bad things may happen. In any case, time to check on Android if the bypass is
indeed working, so we open a file manager app, and head to some other app data
through the newly created BYPASS directory and:
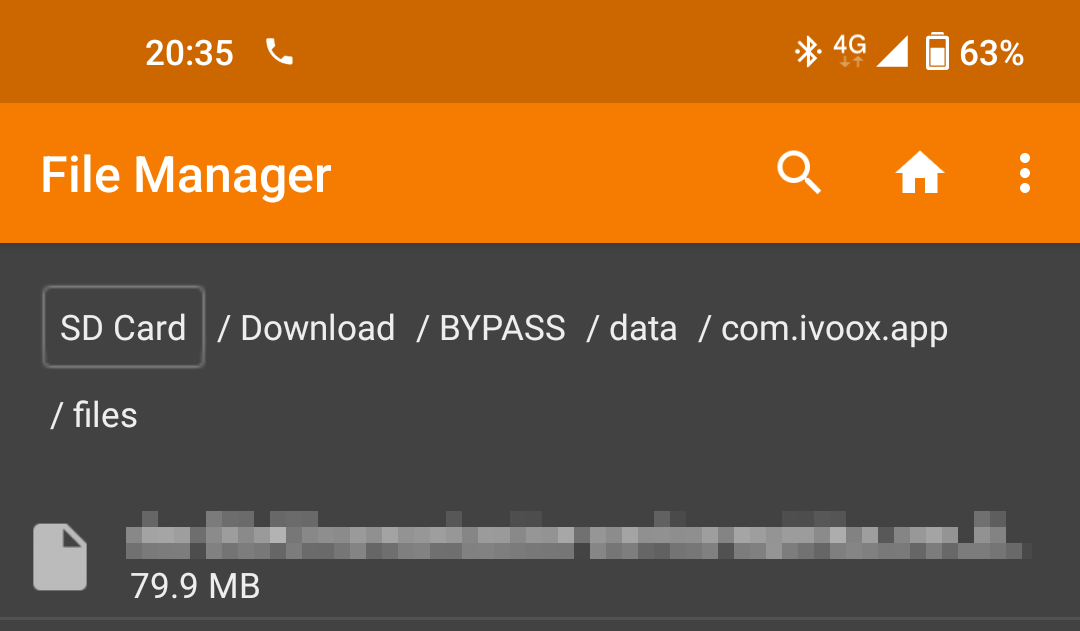
There it is, the app private data is again available for all to see.